Beyond The Headlines
Stay updated with the latest news and insights from around the world.
RFID: The Invisible Handshake Changing How We Connect
Discover how RFID technology is revolutionizing connections and transforming our interactions. Dive into the invisible handshake shaping our future!
Understanding RFID Technology: How It Works and Its Applications
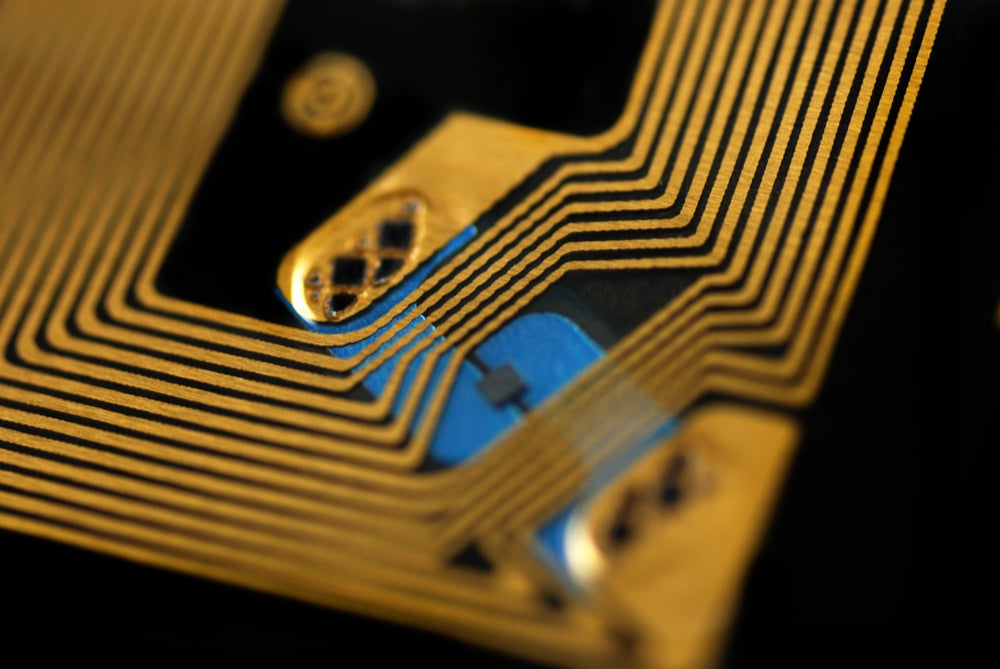
RFID technology, or Radio Frequency Identification, is a innovative method of automatic identification that utilizes electromagnetic fields to transfer data between a reader and a movable tag. This technology consists of three main components: the RFID tag, the RFID reader, and the antenna. The RFID tag contains a microchip and an antenna, which store and transmit data. When an RFID reader emits a radio frequency, the tag is activated and sends the information back to the reader. This process occurs in mere milliseconds, making RFID technology incredibly efficient compared to traditional barcode scanning.
The applications of RFID technology are diverse and continuously expanding. Businesses utilize it for inventory management, allowing for real-time tracking of products and materials, which enhances efficiency and reduces costs. Furthermore, RFID technology is pivotal in sectors like healthcare, where it is used to track medical equipment and ensure patient safety. Other notable applications include access control systems, public transportation fare collections, and even personal security tags for valuable items. As this technology evolves, its potential for innovation and improved service delivery in various industries is promising.
Counter-Strike is a tactical first-person shooter video game that has gained immense popularity in the esports community. Players team up as either terrorists or counter-terrorists, engaging in various objective-based game modes that require strategic planning and teamwork. The game has evolved significantly since its release, spawning multiple versions and updates that enhance gameplay and graphics.
Additionally, you might find useful information on Top 10 Alternatives to Bluetooth Trackers that could enhance your gaming experience.
The Future of Connectivity: RFID's Role in Smart Cities and IoT
As urban areas continue to expand, the concept of smart cities is becoming more prevalent, with technology at the forefront of this evolution. At the heart of this transformation is RFID (Radio Frequency Identification), which plays a crucial role in enhancing connectivity among devices and infrastructure. By leveraging RFID technology, municipalities can effectively manage resources, streamline operations, and improve overall efficiency. For example, RFID tags can be embedded in public transportation systems to provide real-time tracking, helping citizens plan their journeys more effectively and reducing congestion in busy urban areas.
Moreover, the integration of IoT (Internet of Things) with RFID technology creates a network of interconnected devices that can communicate seamlessly with one another. This synergy enables real-time data collection, which is essential for making informed decisions regarding energy management, waste collection, and public safety. As we look to the future, the role of RFID in smart cities will only grow stronger, paving the way for innovative solutions that enhance the quality of life for residents while also contributing to sustainable urban development.
Is RFID Secure? Addressing Common Concerns and Myths
Radio-Frequency Identification (RFID) technology has become increasingly popular for tracking and managing assets, but concerns about its security continue to rise. Many people worry that RFID tags can be easily hacked or that unauthorized individuals can read them from a distance. These fears have led to the spread of several myths surrounding RFID technology. In reality, while RFID systems can be vulnerable if not properly secured, many manufacturers are continuously improving their security measures to address potential risks. For instance, encryption and secure communication protocols can be implemented to protect sensitive data transmitted by RFID tags.
Another common misconception is that RFID is inherently insecure due to its wireless nature. However, it is important to understand that RFID security does not solely depend on the technology itself but also on how it is deployed. Organizations can employ various security techniques, such as limiting access to the RFID system and using authentication methods, to mitigate risks. Furthermore, understanding the differences between active and passive RFID systems can also help users make informed decisions about their security needs. While it is essential to acknowledge the potential vulnerabilities, it is equally important to recognize that with proper precautions, RFID technology can be used safely and effectively.